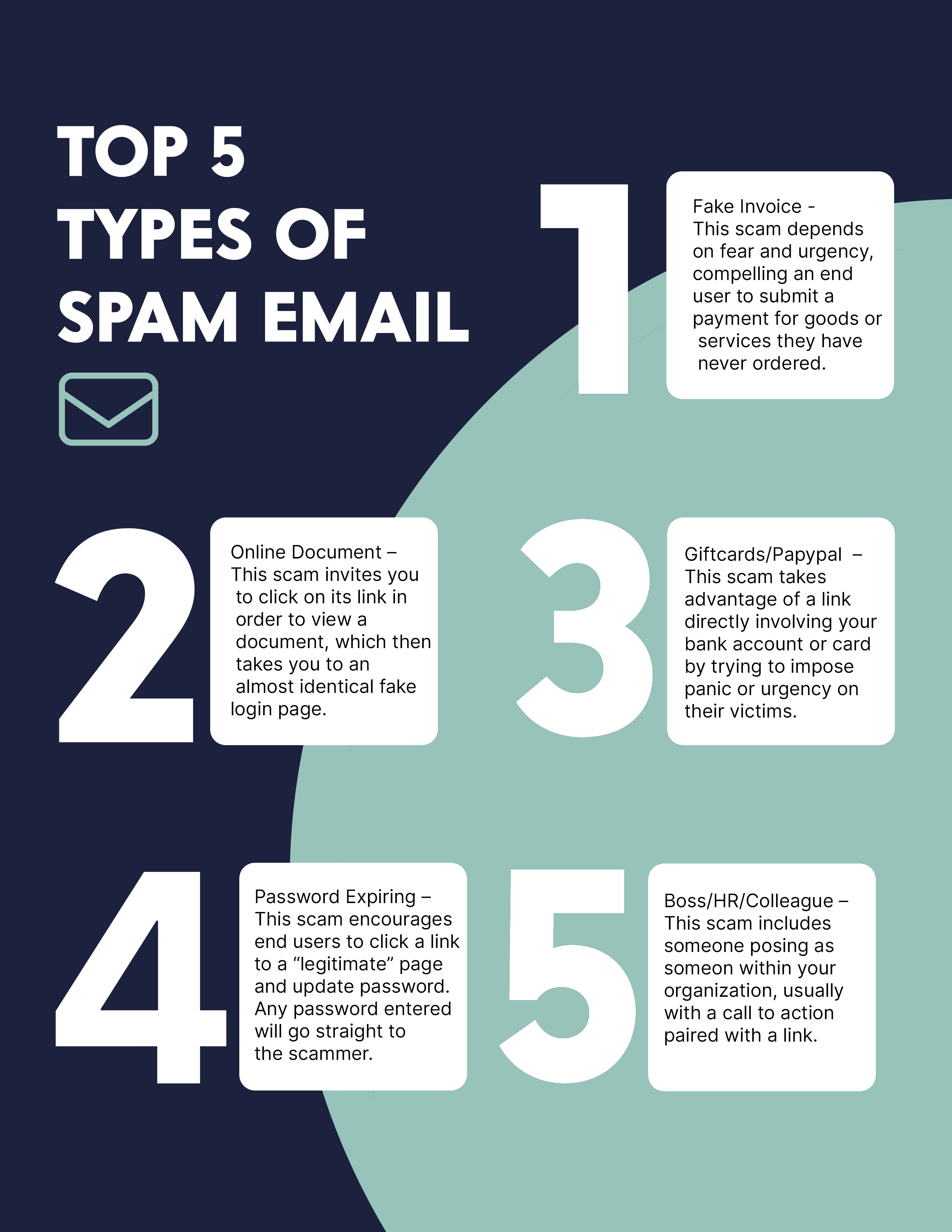
Types of Spam Emails
What is Email Spam? Email spam is unsolicited, unwanted digital communication that is transmitted in large quantities. Spam is a pain, but it also poses a danger. Attackers transmit their unwanted messages in mass through a variety of communication channels. Some spam communications could deceive you into giving out personal information, transmit malware, or scare you into believing you need to pay to get out of trouble. Delete links from spam. The urgency of dangerous spam emails can make you feel pressured to take action.
Since there are so many types, making a single list becomes much more difficult. Nevertheless, we have one. The five most typical types of email spam are listed below.
- Fake Invoice
Invoice fraud in which a third party fraudulently seeks payment. This scam depends on fear and urgency, compelling an end user to submit a payment for goods or services they have never ordered.
Scammers may net large profits; invoice fraud is a common and very effective type of business email hack. It can be relatively simple to con you with a fake email invoice if your company handles hundreds or thousands of invoices each month.
- Online Document
Fake Online logins/portals in which attackers steal your personal information. This scam invites you to click on its link in order to view a document, which then takes you to an almost identical fake login page.
Every cyberattack and data breach tends to entail some kind of phishing attempt to get login information, conduct unauthorized transactions, or deceive a victim into downloading malware. Spam emails come in many forms, and they can be used for malicious purposes such as phishing or identity theft. One type of spam email is an online document, which can contain malicious links or attachments that can be used to infect computers with malware.
- Gift Cards/PayPal
Gift Card Fraud In an email message, the sender will express some level of urgency, such as the fact that they are already busy or about to enter a meeting and urgently need your assistance. This scam takes advantage of a link directly involving your bank account or card by trying to impose panic or urgency on their victims.
You might be asked to pay for anything by loading funds onto a gift card, such as an iTunes or Google Play card, then providing the recipient the numbers on the back of the card. They are attempting to con you if they ask you to do this. No legitimate company or coworker will ever demand that you pay them with a gift card. Anyone who requests payment with a gift card should verify the request with the person directly or over the phone to avoid falling victim to a scam.
- Password Expiring
An email that warns you that your password is about to expire is a fraud designed to get you to divulge private information (such as your password, phone number, or credit card information), download malware, or grant access to your online accounts. This scam encourages end users to click a link to a “legitimate” page and update password. Any password entered will go straight to the scammer. This scam includes someone posing as someone within your organization, usually with a call to action paired with a link.
Spam emails are unsolicited emails that are sent out to a large number of people with the intention of promoting a product or service. One type of spam email is the “password expiring” email, where users are warned that their password will expire soon and they must click on a link to reset it. These emails often contain malicious links and can be used by hackers to gain access to user accounts. It is important for users to recognize these types of spam emails and take the necessary steps to protect their accounts from being compromised.
- Boss/HR/Colleague
An impersonation attack is a type of fraud in which the perpetrators pretend to be a well-known or reliable individual in order to trick a victim into sending cash to a fraudulent account, disclosing private information (like intellectual property, financial information, or payroll information), or disclosing login information that the perpetrators can use to break into a company’s computer network.
Sometimes they identify as a company executive (the boss, the CEO, and high-ranking supervisors), as well as their emails, usernames, passwords, and work titles, are sought after by scammers. They send emails to lower staff while posing as a dependable boss. Scammers attempt to withdraw or collect funds sent by victims.
Scammers frequently target the human resources (HR) division of businesses in an effort to convince employees to change their direct bank deposit information to one that is in their possession.
